Data Privacy vs. Data Security: Differences & How They Work Together
We explore the nuanced world of data management, with a focus on privacy and security. Learn what sets these concepts apart and why they are important now more than ever.
We explore the nuanced world of data management, with a focus on privacy and security. Learn what sets these concepts apart and why they are important now more than ever.
Scandals involving the misuse of personal data have frequented headlines in the past few years. In a world where data has been coined “the new oil,” cyber criminals have also cropped up to take advantage via tactics like phishing, Trojan Horse malware, and more.
When we talk about data protection, we often veer between two distinct but related topics: data privacy and data security. At first glance, these two things may seem the same, but they’re actually distinct levers for data protection.
Data privacy is the act of protecting information from unauthorized collection, storing, or sharing. It most often refers to digital data, especially personally identifiable information (PII). Data privacy is concerned with protecting an individual’s right to have a say in how their data is being collected and used.
Regulations and laws regarding data privacy have been around for decades, but they’ve continued to pick up steam in recent years. In 2018, the GDPR acted as a touchstone moment in the privacy landscape, setting a global precedent on how personal data should be processed and stored by the organizations that collect it. (Moreover, it gave individuals the ability to dictate how their personal data could be used.)
Data security refers to the safeguarding of customer data from those who wish to access or use it without permission (e.g., identity theft, cyberattacks). It involves techniques like data encryption, employee education on best practices (e.g., never downloading an email attachment from a suspicious or unknown entity), or regularly auditing systems to detect any vulnerabilities.
While there is certainly overlap between data privacy and data security, the key thing to remember is:
Data privacy is concerned with how an individual’s data is collected, used, and stored – assuring compliance with applicable privacy laws and regulations.
Data security is focused on protecting data from cyberattacks or unauthorized users, and the threat of data theft, corruption, or breaches.
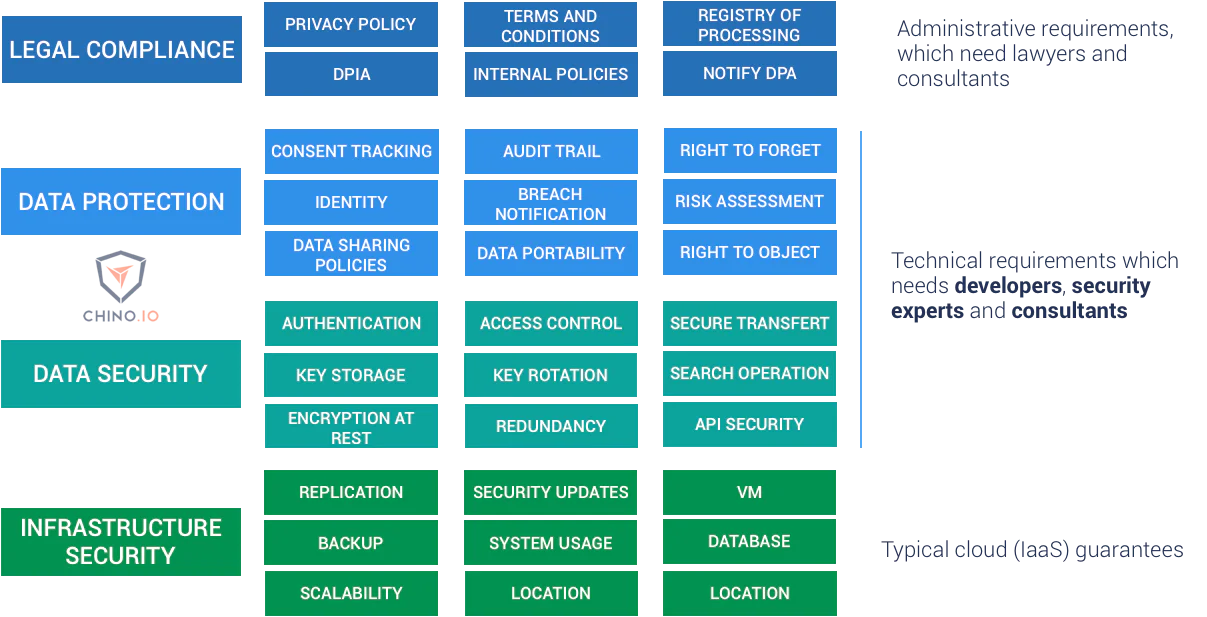
Protecting customer data isn’t a simple task. The regulatory landscape is changing rapidly, and generative AI’s popularity has dredged up concerns over how to protect personal data from sneaking into training models.
However, with the right infrastructure, permission controls, and internal policies, effective data privacy at scale is attainable. Here’s how to lay the right foundation.
Protecting customer privacy is both an ethical and legal matter. Understanding which laws and regulations you’re beholden to is essential – not just to stay compliant, but to secure trust with your customers. We’ve mentioned the GDPR, one of the most famous data privacy laws currently. And while the GDPR covers EU residents, it also applies to any business that has customers in that region (no matter where that company is based).
Here are just a few things to consider when trying to understand which privacy laws apply to your business.
Are you in a highly regulated industry like healthcare or finance, which have their own regulations? For instance, the Health Insurance Portability and Accountability Act of 1996 or HIPAA or the Gramm-Leach-Bliley Act.
Data residency laws. Are you required to collect, store, and process data in the region your customers are in?
Data resiliency. How prepared is your business to prevent or recover from an interruption like a system failure, cyberattack, or power outage? Here’s an excerpt of how Twilio handles resilience, from our Security policy:
18.1 Resilience. The hosting infrastructure for the Twilio Services and Segment Services (a) spans multiple fault-independent availability zones in geographic regions physically separated from one another and (b) is able to detect and route around issues experienced by hosts or even whole data centers in real time and employ orchestration tooling that has the ability to regenerate hosts, building them from the latest backup.
Interested in learning more? We compiled a list of 16 data privacy training courses worth checking out.
Customers own their data, including their name, email address, and cell phone number – and to use this data, you need their explicit permission. That means informing them of how their information will be used, and giving them the chance to agree and to opt-in.
At Segment, we created an open source Consent Manager to help automate the process of requesting user consent, storing user preferences on privacy, and updating these preferences at the user’s request.
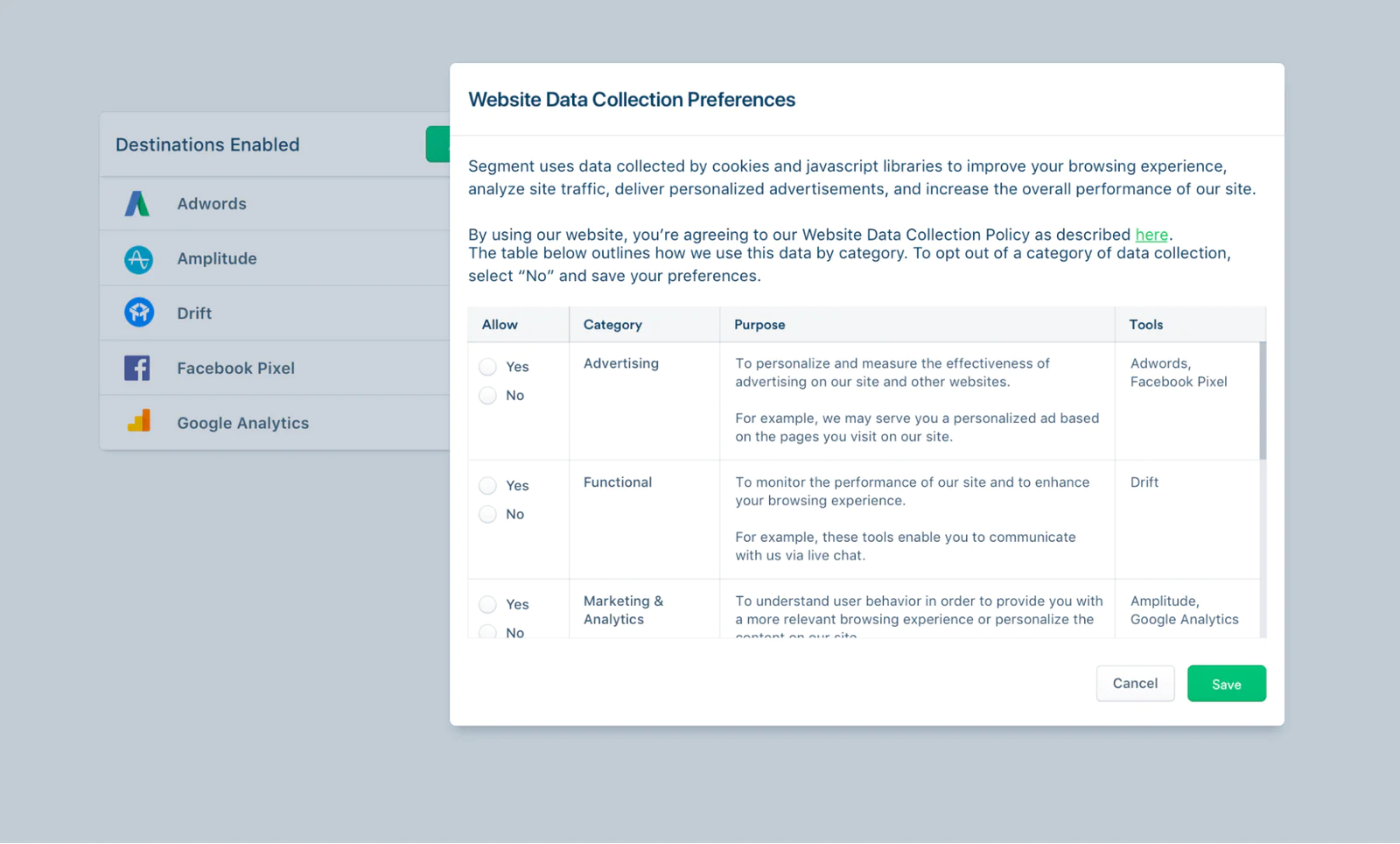
Even if you have to collect sensitive data (like credit card information, health records, etc.), not everyone in your organization should have access to it. To protect confidentiality and strengthen security, we recommend classifying data according to its level of risk (and there are ways to automate this). For example, someone’s social security number should be considered highly sensitive information, whereas their job title would be considerably less risky.
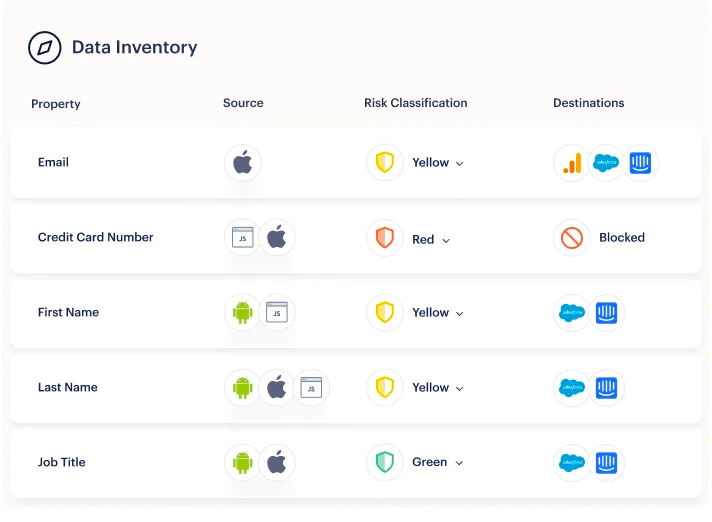
After classifying this data, businesses can then implement role-based access controls to control who has access and visibility into these different types of data. .
How can you ensure that data stays safe and away from prying eyes? Consider these must-dos for companies of every size.
You can’t make up data security as you go; having a clear, well-documented policy is essential. This data security policy often includes:
The specific certifications and attestations your business has (e.g., ISO 27001, SO2 Compliance, etc.). At Twilio’s Segment, our security framework is based on the ISO 27001 Information Security Management System with programs covering: Policies and Procedures, Asset Management, Access Management, Physical Security, Operations Security, Communications Security, Business Continuity Disaster Recovery Security, Cloud and Network Infrastructure Security, and more.
How you’re classifying data by risk level.
What controls are in place to limit who internally has access to data (e.g., principle of least privilege).
A plan of action in the event of a data breach or security incident. For instance, Twilio policies are in line with NIST SP 800-61 (the National Institute of Standards and Technology’s Computer Security and Incident Handling Guide).
Regular auditing of how data is handled and stored throughout its lifecycle, the systems, tools, hardware being used, current user permissions (and so forth) to ensure compliance.
For more on how Segment handles security and compliance, check out this guide.
Risk assessments are a key component of data security – when businesses assess potential threats or uncertainties and what impact they could have on the organization. Conducting a risk assessment is crucial from spotting potential weak spots before they’re taken advantage of by bad actors, and for having the proper plans and procedures in place should the worst case scenario occur.
For instance, a risk assessment could uncover that certain teams are storing passwords to specific apps and tools in a shared doc. After discovering this, a business could implement stronger security features, like single sign-on (SSO) or multi-factor authentication (MFA).
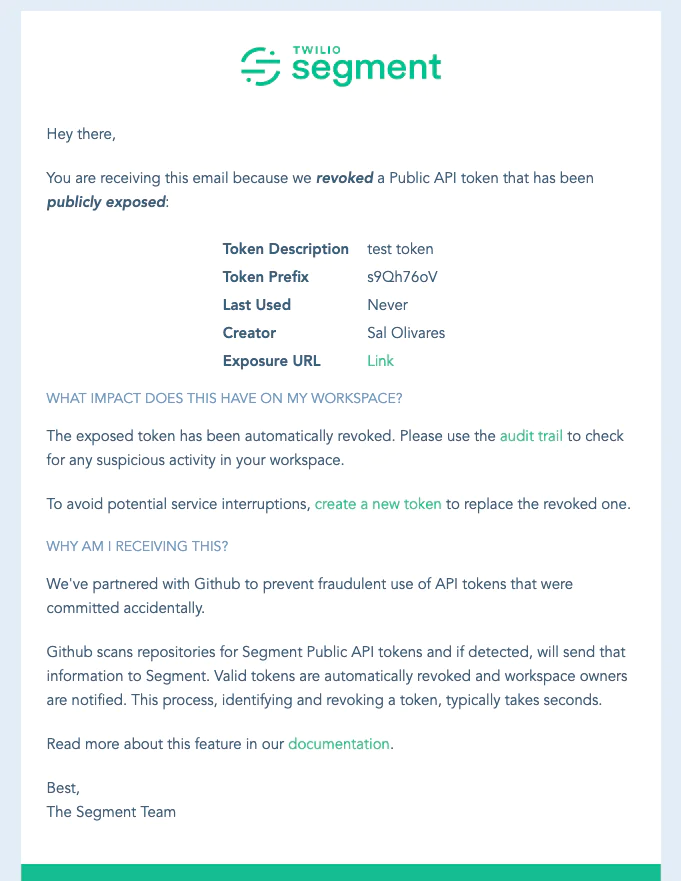
At Segment, we currently monitor sites like GitHub for orphaned or compromised API tokens, and revoke any tokens that become public. Customers then get a notification of this revocation, along with guidance on how to monitor for data security issues.
An email notification for when a Public API token has been publicly exposed, and automatically revoked.
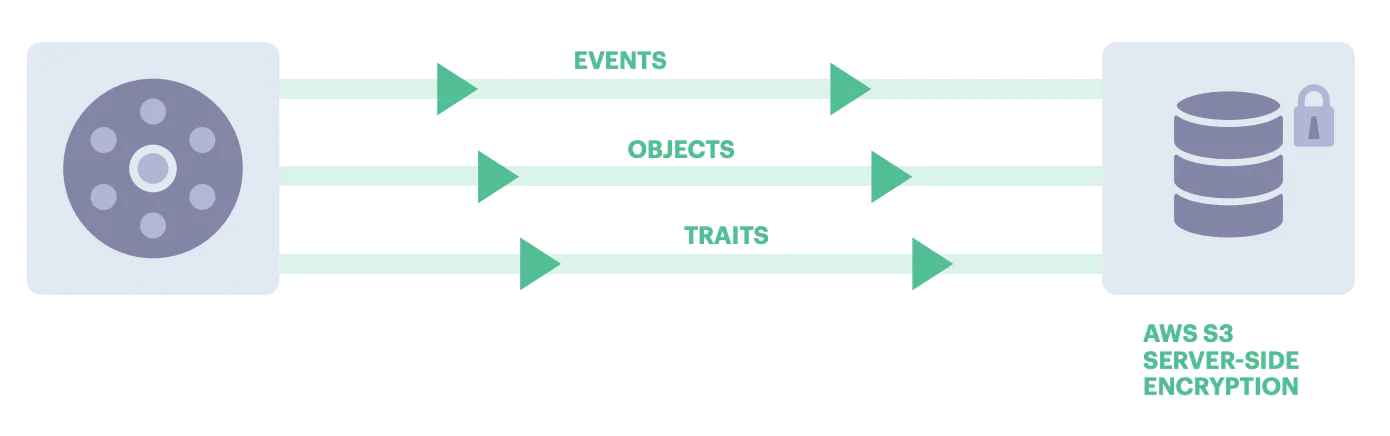
Data should be encrypted both at rest and in transit to ensure its protection.
You can protect data as it’s being transmitted with the Transport Layer Security (TLS) protocol and use hash technology to hide passwords. Any tools or cloud providers should also use encryption at all levels.
For customers using Segment to send data to a warehouse (Redshift, Snowflake, etc.), your data will be stored inside the data warehouse that you own, manage, and secure.
In addition to limiting internal access to data and data tools, carefully consider how much data you allow your vendors and integrations to view or use. Many tools ask that you grant the maximum access by default. You can limit risk by reviewing each permission and only approving those necessary to do business.
Review these permissions regularly, revoking those that no longer make sense. If an app or integration hasn’t had a security update in a while, it may no longer fit your high threshold for vendors and may need to be replaced. Incorporate rigorous data privacy training for your employees so that team members know how data should be shared. This may include new generative AI apps, like ChatGPT, that may save customer data for future machine learning uses and not keep customer data private at all.
Connect with a Segment expert who can share more about what Segment can do for you.
We'll get back to you shortly. For now, you can create your workspace by clicking below.
Criminals will always come up with new ways to steal data, whether it’s through a counterfeit app or a sophisticated new hacking method. New concerns for data include:
Generative AI. Employees may put sensitive data directly into these tools without understanding how this data may be collected and used to “train” the AI. This unauthorized sharing of data may cause big problems for companies that don’t address it proactively.
Business use conflicts. Companies may struggle to balance the personalization that consumers want when they use apps, view media, or shop online with the privacy they demand. Since personalization requires some level of customer data management to work, companies should strive to use only the data needed to serve customers better while protecting that data from unhelpful or even unauthorized uses.
Segment helps businesses protect data and respect privacy while providing unique and useful customer insights that can help you grow your business in a digital, omnichannel environment.
Both data security and data privacy matter, and businesses should make great efforts to ensure customers have high levels of both. Security would involve protecting their information from hackers, providing safe payment processing, and ensuring they don’t fall victim to cybercrimes. Privacy ensures that their data is only collected, stored, or accessed with their permission.
AI can sort through large amounts of customer data to help identify the most sensitive data that companies need to protect. It can also detect patterns that may signal a security breach or an opportunity to prevent one. ML uses these trends in data to create better, more secure systems and provide businesses with insights for improving their data privacy and security practices.
Segment makes it simple to categorize the fields of even large amounts of customer data into green, yellow, or red risk groups (to signify their level or risk and sensitivity). You can quickly limit access to data based on category, update customer data to meet new regulations, or even remove data in real time based on customer requests. It also helps you block the data that you don't want the customer to share with you, such as passwords or credit card numbers.
Segment facilitates data privacy and protection by limiting access to certain types of information, using data encryption, and enforcing password protection. We also secure data at rest by keeping metadata separate from customer data, which is securely stored in Amazon S3.
In the event of an unlikely compromise, Segment will do a thorough review of the type of data that was included in the breach, as well as take steps to prevent further access to this data. Segment customers will be notified of what to expect and any action they need to take to further secure their own data and customer data. Questions about what Segment is doing to protect your data can be directed to us anytime at support@segment.com.
Enter your email below and we’ll send lessons directly to you so you can learn at your own pace.